Apple announced a suite of security and privacy improvements on Wednesday that the company is pitching as a way to help people protect their data from hackers, including one that civil liberty and privacy advocates have long pushed for.
The tech giant will soon allow users to choose to secure more of the data backed up to their iCloud using end-to-end encryption, which means no one but the user will be able to access that information.
Apple says the changes will help users protect their digital lives from hackers in the exceptional case that an advanced state actor was able to breach the company servers.
But privacy advocates like Albert Fox Cahn, founder of the Surveillance Technology Oversight Project, say these changes may have a more immediate effect on the types of user data law enforcement and government agencies can get from Apple.
These changes “acknowledge the massive public backlash against expanded spying on our devices”, particularly in the aftermath of the supreme court’s reversal of federal abortion protections, he said.
“This type of protection is most valuable in protecting against not cyber criminals, but people who are abusing government power to force the company to hand over data,” Cahn said. “Apple has long been in the position where it’s had to be the long arm of the police for years. Their law enforcement manual shows dozens of ways that they can help with investigations and now for people who opt into the protection [feature], there will be a safeguard going forward.”
That might be a cause of concern for government agencies looking to secure user data to aid in their investigations. Apple declined to comment on whether the company has discussed the changes with law enforcement or government agencies.
Companies such as Apple have become an increasingly appealing entity for hackers and law enforcement alike due to the vast amounts of information they hold about people.
Recent years have brought a spike in global cyber-attacks and data breaches. In the first quarter of 2022, there were 404 publicly reported data breaches, up 14% from the same quarter in the previous year, according to a report from the Identity Theft Resource Center (ITRC). There was a 68% total increase in data breaches between 2020 and 2021.
The number of law enforcement and government requests for data that Apple has received has also increased, according to the company’s latest transparency report. Between January and July 2021, the company received more than 12,o00 requests for various types of user information, up from more than 10,000 in the last six months of 2020.
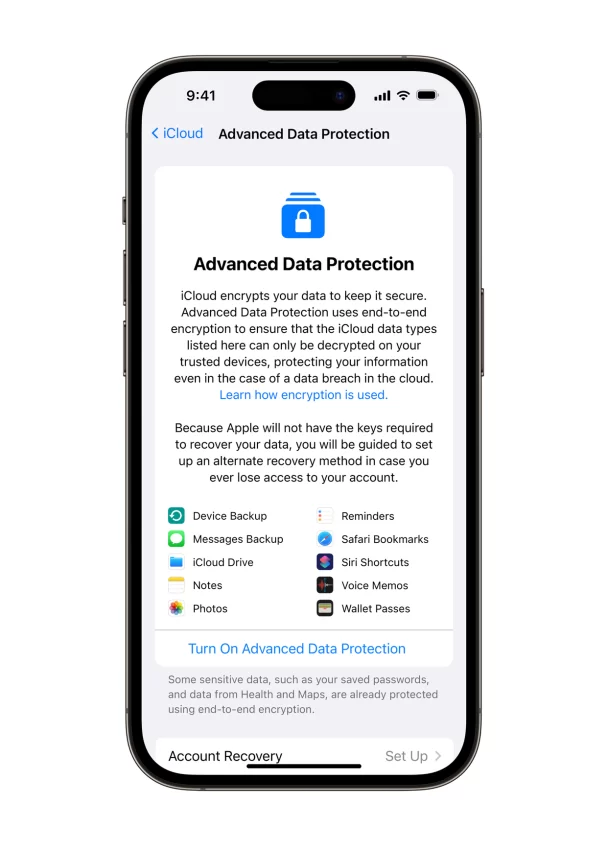
The end-to-end encryption of user information stored on iCloud, which Apple is calling “advanced data protection for iCloud”, will first be rolled out to a small subset of test users before launching widely in the US before the end of the year and globally in 2023. The new offering will mean information such as messages that are backed up to iCloud, notes and photos would be fully encrypted.
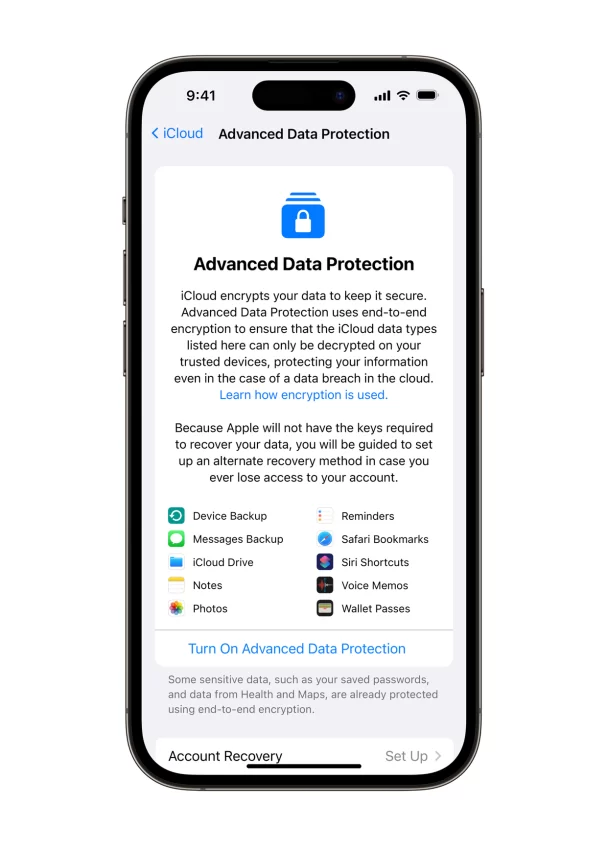
The change will not cover all data, however – contacts, calendar information, and email will not be encrypted – and users will have to voluntarily opt into the feature. The encryption key, or the code used to gain access to that secure data, will be stored on the device. That means that if a user who opts into this protection loses access to their account, they will be responsible for using their key to regain that access – Apple will no longer store the encryption keys in iCloud.
The feature not being turned on for all users by default remains a point of contention for privacy advocates.
“I’m less critical of Apple for [not encrypting contacts, calendar information and email] just given how hard it would be to cut off so many email programs and calendar tools,” Cahn said. “But I do think that having a transition to privacy by default for iCloud is the most important step.”
The company says that it made these features opt-in because the system requires users to be responsible for the encryption keys and other means to regain and recover access to that information. “If you lose access to your account, only you can recover this data, using your device passcode or password, recovery contact, or recovery key,” according to Apple’s website.
In addition to iCloud data protection, Apple plans to roll out a physical security key system for people signing into their iCloud account on any new device. It acts as a hardware-based two-factor authentication system. For those who opt to use this additional layer of security, they will be required to plug a physical security key into the charging port on the phones to verify their identity when they sign into their iCloud account on a new device.
However, users who choose to use this to protect their iCloud accounts will be responsible for holding on to those security keys – the main key and a backup.

Lastly, the company is rolling out a code system that allows people to verify that their messages are only going to the intended recipient and not being compromised by a hacker. The process may be familiar to users of the encrypted messaging app Signal. In Apple’s case, two people who have enabled the system will be able to exchange their unique code and their devices will automatically detect whether someone with a different code has entered the conversation. Automatic alerts will pop up in conversations between users who have enabled this verification feature “if an exceptionally advanced adversary, such as a state-sponsored attacker, were ever to succeed breaching cloud servers and inserting their own device to eavesdrop on these encrypted communications”, the company said in the news release announcing the products.
Read more:
Apple announces new security and privacy measures amid surge in cyber-attacks